EXPERIMENT No-9
OBJECT: Simulation of Cisco Port Security
REQUIRED SOFTWARE: Cisco Packet Tracer 8.1.1
Packet Tracer- Configuring Switch Port security
Addressing Table
| Device | Interface | IP address | Subnet Mask |
| S1 | VLAN1 | 10.10.10.2 | 255.0.0.0 |
| PC1 | NIC | 10.10.10.10 | 255.0.0.0 |
| PC2 | NIC | 10.10.10.11 | 255.0.0.0 |
| Rough Laptop | NIC | 10.10.10.12 | 255.0.0.0 |
Objective
Part 1: Configure Port Security
Part 2: Verify Port Security
Background
In this activity, you will configure and verify port security on a switch. Port security allows you to restrict a port’s ingress traffic by limiting the MAC address that are allowed to send traffic into the port.
Part 1: Configure Port Security
- Access the command line for S1 and enable port security on Fast Ethernet ports 0/0 and 0/2.
- Set the maximum so that only one device can access the Fast Ethernet ports 0/1 and 0/2.
- Secure the ports so that the MAC address of a device is dynamically learned and added to the running configuration.
- Set the violation so that the Fast Ethernet ports 0/1 and 0/2 are not disabled when a violation occurs, but packets are dropped from and unknown source.
- Disable all the remaining unused ports, Hint: Use the range keyword to apply this configuration to all the ports simultaneously.
Part 2: Verify Port Security
- From PC1 ping PC2.
- Verify port security is enabled and MAC address of PC1 and PC2 were added to the running configuration.
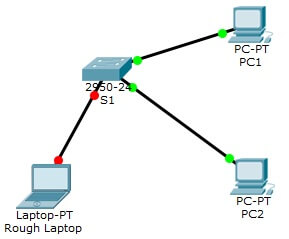
- Attach Rouge Laptop to any unused switch port and notice that the link lights are red.
- Enable the port and verify that Rouge Laptop can ping PC1 and PC2. After verification shutdown the port connects to Rouge Laptop.
- Disconnect PC2 and connect Rouge Laptop to PC2’s port. Verify that Rouge Laptop is unable to ping PC1.
- Display the port security violations for the port Rouge Laptop is connected to.
- Disconnected Rouge Laptop and reconnect PC2 verify PC2 can PC1.
- Why PC2 is able to ping PC1, but the Rouge Laptop is not?
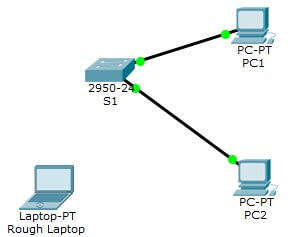
Network Diagram
Setup this network:
Switch>en Switch#config t Switch(config)#hostname S1 S1(config)#int range fastEthernet 0/1-2 S1(config-if)# switchport mode access S1(config-if)# switchport port-security S1(config-if)# switchport port-security maximum 1 S1(config-if)# switchport port-security mac-address sticky S1(config-if)# switchport port-security violation shutdown S1(config-if-range)#exit S1(config-if)#int range fa0/3-24 S1(config-if-range)#shutdown
Go to PC1 & ping PC2
PC>ping 10.10.10.11
Pinging 10.10.10.11 with 32 bytes of data:
Reply from 10.10.10.11: bytes=32 time=0ms TTL=128
Reply from 10.10.10.11: bytes=32 time=15ms TTL=128
Reply from 10.10.10.11: bytes=32 time=14ms TTL=128
Reply from 10.10.10.11: bytes=32 time=0ms TTL=128
S1#show port-security interface fastEthernet 0/1
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
Secure Static Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 1
Last Source Address:Vlan : 0060.5C70.6530:1
Security Violation Count : 0
Go to PC2 & ping PC1
PC>ping 10.10.10.10
Pinging 10.10.10.10 with 32 bytes of data:
Reply from 10.10.10.10: bytes=32 time=23ms TTL=128
Reply from 10.10.10.10: bytes=32 time=9ms TTL=128
Reply from 10.10.10.10: bytes=32 time=9ms TTL=128
Reply from 10.10.10.10: bytes=32 time=14ms TTL=128
PC>ping 10.10.10.11
Pinging 10.10.10.11 with 32 bytes of data:
Reply from 10.10.10.11: bytes=32 time=0ms TTL=128
Reply from 10.10.10.11: bytes=32 time=15ms TTL=128
Reply from 10.10.10.11: bytes=32 time=14ms TTL=128
Reply from 10.10.10.11: bytes=32 time=0ms TTL=128
S1#show port-security interface fastEthernet 0/2
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 1
Last Source Address:Vlan : 0090.21CD.A69E:1
Security Violation Count : 0
S1#show mac-address-table
Mac Address Table
——————————————————-
Vlan Mac Address Type Ports
——- ——————– ——– ———
1 0060.5c70.6530 STATIC Fa0/1
1 0090.21cd.a69e STATIC Fa0/2
S1#show port
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action
(Count) (Count) Count)
—————————————————————————————————————–
Fa0/1 1 1 0 Shutdown
Fa0/2 1 1 0 Shutdown
—————————————————————————————————————–
After that Add 3 PC via cable
Go to PC1 & ping PC2
Go to PC2 & ping PC1
Pinging 10.10.10.10 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
S1#config t S1(config)#int fa0/3 S1(config )#no shut S1(config )#shutdown
Cut 3rd PC wire
Cut 2nd PC wire
Joint 3rd PC wire in fa0/2
PC>ping 10.10.10.10
Pinging 10.10.10.10 with 32 bytes of data:
Reply from 10.10.10.10: bytes=32 time=23ms TTL=128
Reply from 10.10.10.10: bytes=32 time=9ms TTL=128
Reply from 10.10.10.10: bytes=32 time=9ms TTL=128
Reply from 10.10.10.10: bytes=32 time=14ms TTL=128
S1#config t S1(config)#int vlan 1 S1(config-if)#ip add 10.10.10.2 255.0.0.0 S1(config-if)# no shut
Protect:—The PFC (Policy Feature Card ) drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value.
Restrict: — In restrict mode frames from non-allowed address would be dropped. But in this mode, switch will make a log entry and generate a violation alert and the violation counter increments.
Shutdown:—Puts the interface into the error-disabled state immediately and sends a trap notification.
Example
Switch#sh port
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action
(Count) (Count) (Count)
—————————————————————————
Fa0/1 2 2 1 Shutdown
Fa0/2 2 2 0 Protect
Fa0/3 2 2 7 Restrict
—————————————————————————
What is Port Security
It is quite easy for any hacker or attacker to access a network incorrectly when they are able to enter the network. In this case, Ethernet LANs are very weak as all their switch ports can be used by anyone. This can result in a number of attacks such as a DOS attack on layer two or an address spoofing attack. If the network of the organization is secure, the feature used to control all such switch ports is called Port Security.
To secure any port, the user has to follow these two steps:
- The number of MAC addresses on any single port has to be reduced. So that we can use fewer PCs. For example, if MAC Address is reduced to 1, then we will be able to use only one PC. It benefits from this that if any port has more MAC addresses than set or confined. Then appropriate action can be taken. Example: MAC Address 1 has been set and as soon as another PC is installed, its MAC address will change, and then we will easily fined out that another PC has been accessed on this port.
- If one gets access information of any permission, then using any option, traffic can be stopped immediately or the user can generate a log-message, which can cause external access to be captured.
Switches know the MAC address only when the frame is sent by the switch port. Using port security, the user can limit the number of times a MAC address is learned by a switch.
Port security Modes
There are three ways we can secure Port
- Protected
- Restrict
- Shutdown
Protect– In this, we bind the PC to the MAC address and as soon as another PC is installed we send the packet, then it ends the packet and does not let it go forward because it does not get the MAC address right.
Restrict– In this, we bind the PC to the MAC address and as soon as another PC is installed we send the packet, then it ends the packet and does not let it go forward because it does not get the MAC address right. It performs the same function as the Protect. This means that it also continues to drop packets until you delete all MAC addresses that exceed the maximum limit. Apart from this it also generates a log-message, increases the value of counter and also sends SNMP trap.
Shut down– This mode is preferred over the banked mode as it closes the port forever when information is received on any port without permission. It also generates log-messages, sends SNMP traps and increases the value of the counter. It keeps the port closed until the manager removes it via the “No Shutdown” command.
Sticky– This is not a violation mode. Using this command, the user can provide static MAC address security without having to type absolute MAC address. For example, if the user gives the maximum limit of 2, then the first 2 MAC addresses that are learned on the port will be put in the running-configuration. And if a third MAC address is found there, then action can be taken by using the appropriate violation code.
Note– Port Security only works in access mode, which means that the user must first make it an access mode to enable port security.
Port security configuration
Enable port security on the Switch’s Fa0 / 1 interface. First of all, the port has to be converted into an access port so that port security is enabled.
S1(config)#int fa0/1
S1(config-if)#switchport mode access
S1(config-if)#switchport port-security
Use Sticky Command as it learns the MAC address dynamically
And establishes a limit after which appropriate action can be taken:
S1(config-if)#switchport port-security mac-address sticky
S1(config-if)#switchport port-security maximum 2
S1(config-if)#switchport port-security violation shutdown
If the user wants to give a static entry, it can do so by stating the MAC address:
S1(config-if)#switchport port-security mac-address aa.bb.cc.dd.ee.ff
If you have any question or suggestion related to this Experiment, you can write it in the comment box below.
Download Cisco Packet Tracer 6.22
Download Cisco Packet Tracer 8.1.1
MCQ-SET 1
Dear Students, This Purpose of Preparation of Computer Network Online Test is in 30 Questions English. There is a collection of questions asked in the CCNA Exam. On answering each question one point will be given. And it is mandatory to bring 50% marks to pass. To start the test you have to click on Start Button. All the questions will have to be answered. Go to Last and click on Finish Button, after which your Result will appear on the screen. After clicking Finish, there will be three option shows below 1.Restart Quiz 2.View Question 3.Show Leader-board. After filling your name and e-mail id by clicking on the show leader-board, click on send, after which your result will be shown.
MCQ-SET 2
25
Both A & B
SNMP
Layer 1 to Layer 3
Both A & B
All of these
Logical ring
One-byte
IEEE 802.3 or CSMA/CD bus
32 bit
Filtering function
Serial Line IP
20/21
Asynchronous transfer mode
Both A & B
Both A & B
Both A & C
Both A & B
internet
Autonomous
broadcasting
unicasting
peers
cells
internet
category5
multimode
frequency
server
star
